Nginx反向代理的主被动健康检查方式
作者:XL's妃妃
这篇文章主要介绍了Nginx反向代理的主被动健康检查方式,具有很好的参考价值,希望对大家有所帮助,如有错误或未考虑完全的地方,望不吝赐教
一、环境介绍
1、系统:centos7
2、应用部署:weblogic 12c
2、nginx版本:nginx-1.7.2
3、应用1(weblogic1):192.168.29.149:7018/realware
4、应用2(weblogic2):192.168.29.150:7012/realware
5、nginx服务器:192.168.29.152:8080
二、下载nginx-1.7.2
mkdir -p /opt/src cd opt/src wget http://nginx.org/download/nginx-1.7.2.tar.gz tar -xvf nginx-1.7.2.tar.gz
三、下载主动健康检查插件
cd opt/src yum -y install wget wget https://codeload.github.com/yaoweibin/nginx_upstream_check_module/zip/master yum install unzip -y unzip master.zip
四、安装主动健康检查插件
yum install patch -y cd /opt/src/nginx-1.7.2 patch -p1 < /opt/src/nginx_upstream_check_module-master/check_1.7.2+.patch
五、编译安装nginx
cd /opt/src/nginx-1.7.2 yum -y install gcc pcre-devel zlib-devel openssl openssl-devel ./configure --prefix=/usr/local/nginx --add-module=/opt/src/nginx_upstream_check_module-master make make install
六、反向代理被动健康检查与反向代理主动健康检查
1、反向代理被动健康检查
配置文件修改:vim /usr/local/nginx/conf/nginx.conf
#user nobody;
worker_processes 1;
error_log logs/error.log;
error_log logs/error.log notice;
error_log logs/error.log info;
pid logs/nginx.pid;
events {
worker_connections 1024;
}
http {
include mime.types;
default_type application/octet-stream;
sendfile on;
keepalive_timeout 65;
#upstream 后面要用nginx所在服务器的IP,不然可能会导致网络的css、js等外部连接无法调用。
upstream 192.168.29.152 {
#以5s为周期,5秒内只要有一次访问失败,则这5s内不会再向该ip发起访问。可以根据情况调整。
server 192.168.29.150:7012 max_fails=1 fail_timeout=5s;
server 192.168.29.149:7018 max_fails=1 fail_timeout=5s;
}
server {
listen 8080;
#server_name 后面要用web应用的名称
server_name realware;
location / {
proxy_pass http://192.168.29.152; #这里的IP要与upstream保持一致。
proxy_set_header X-Forwarded-Host $host;
proxy_set_header X-Forwarded-Server $host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header Host $host:$server_port;
}
}
}
2、反向代理主动健康检查
配置文件修改:vim /usr/local/nginx/conf/nginx.conf
#user nginx;
worker_processes 1;
error_log /usr/local/nginx/logs/error.log info;
#er
#ror_log logs/error.log notice;
#error_log logs/error.log info;
pid /usr/local/nginx/logs/nginx.pid;
# worker_rlimit_nofile 65535;
events
{
# use epoll;
worker_connections 65535;
}
http
{
include mime.types;
default_type application/octet-stream;
log_formmat main '$remote_addr - $remote_user [$time_local] "$request" '
'$status $body_bytes_sent "$http_referer" '
'"$http_user_agent" "$http_x_forwarded_for"';
access_log /usr/local/nginx/logs/access.log main
sendfile on;
#tcp_nopush on;
keepalive_timeout 60;
client_max_body_buffer_size 100m;
client_max_body_size 40m;
upstream realware_service {
server 192.168.29.149:7018;
server 192.168.29.150:7012;
#以10s为一个周期,每隔10snginx会自动向上游服务器发送一次请求,如果超过5s超时且达到3次,则该服务器标记为不可用;
#如果请求次数有一次以上没有超时,这标记为可用
check interval=10000 rise=1 fall=3 timeout=5000 type=tcp default_down=true;
check_http_send "HEAD / HTTP/1.1\r\nConnection: keep-alive\r\n\r\n";
check_http_expect_alive http_2xx http_3xx;
}
upstream realware_stamp {
server 192.168.29.149:7018 weight=5;
server 192.168.29.150:7012 weight=5;
#以10s为一个周期,每隔10snginx会自动向上游服务器发送一次请求,如果超过5s超时且达到3次,则该服务器标记为不可用;
#如果请求次数有一次以上没有超时,这标记为可用
check interval=10000 rise=1 fall=3 timeout=5000 type=tcp default_down=true;
check_http_send "HEAD / HTTP/1.1\r\nConnection: keep-alive\r\n\r\n";
check_http_expect_alive http_2xx http_3xx;
}
server {
listen 8080;
server_name locahost;
add header Access-Control-Allow-Origin *;
add header Access-Control-Allow-Meehods 'GET,POST';
add header Accesg-Control-Allow-Headers 'DNT,x-Mx-ReqToken,Keep-Alive,User-Agent,X-Requested-With,If-Modified-Since,Cache-Control,Content-Type,Authorization'
access_log /usr/local/nginx/logs/access.log main
location /realware {
proxy_connect_timeout 60;#与上游服务器的连接超时时间
proxy_read_timeout 60;#与上游服务器的读取超时时间
proxy_send_timeout 60;#与上游服务器的发送超时时间
proxy_pass http://realware_service;
proxy_set_header X-Forwarded-Host $host;
proxy_set_header X-Forwarded-Server $host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header Host $host:8080;
peoxy_set_header x-Real-IP $remote_addr;
peoxy_set_header REMOTE-HOST $remote_addr;
}
server {
listen 8081;
server_name locahost;
add header Access-Control-Allow-Origin *;
add header Access-Control-Allow-Meehods 'GET,POST';
add header Accesg-Control-Allow-Headers 'DNT,x-Mx-ReqToken,Keep-Alive,User-Agent,X-Requested-With,If-Modified-Since,Cache-Control,Content-Type,Authorization'
access_log /usr/local/nginx/logs/access.log main
location /estamp {
proxy_connect_timeout 60;#与上游服务器的连接超时时间
proxy_read_timeout 60;#与上游服务器的读取超时时间
proxy_send_timeout 60;#与上游服务器的发送超时时间
proxy_pass http://estamp_service;
proxy_set_header X-Forwarded-Host $host;
proxy_set_header X-Forwarded-Server $host;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header Host $host:$server_port;
peoxy_set_header x-Real-IP $remote_addr;
peoxy_set_header REMOTE-HOST $remote_addr;
}
#健康监控页面
location /status {
check_status html;
access_log off;
}
}
}
五、启动nginx
cd /usr/local/nginx/sbin ./nginx
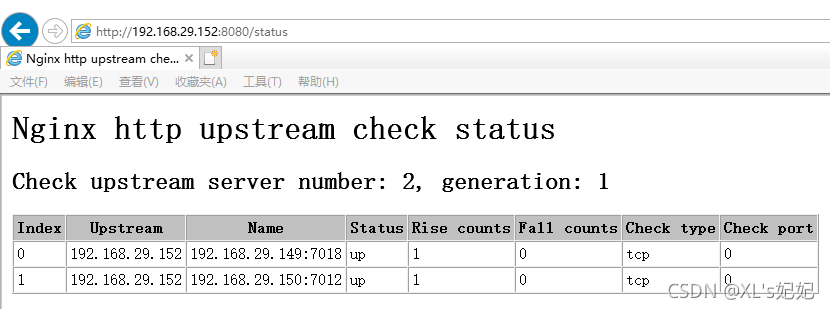
六、检验结果
在浏览器输入http://192.168.29.152:8080/realware 查看是否配置成功;
在浏览器输入http://192.168.29.152:8080/status
总结
以上为个人经验,希望能给大家一个参考,也希望大家多多支持脚本之家。
